ST recently released the STSAFE-V100-Qi, its newest WPC Qi-compliant system on chip, to democratize safe and secure wireless charging in cars. In a nutshell, the solution facilitates the authentication of WPC Qi-certified chargers and compatible devices to enable fast charging up to 15 W. To achieve this, ST based the STSAFE-V100-Qi on the ST33K-A secure element, thus obtaining a hardware CC EAL6+ (Common Criteria Evaluation Assurance Lev-el) certification and providing a solution that is both automotive qualified and works alongside other ST components like ST25R NFC readers.
1st thing to look for: Security tailored to the needs of the automotive industry
Grasping the need for stricter cybersecurity regulations
The reasons for the more demanding security needs come from the fact that car makers and automotive OEMs operate under regulations and standards with more exacting requirements around safety than other industries. As vehicles become increasingly connected and feature-rich, for the convenience and comfort of end-users, industry regulations must also anticipate new and always greater risk factors and threat actors. In the case of a Qi car charger, engineers must protect against a wide range of issues, from over-charging to cloning and data breaches that may threaten the entire vehicle. Cybersecurity in cars is increasingly a hot topic because there are more potential attack surfaces, and the consequences of a breach are ever more damaging.
Understanding the industry initiatives
Consequently, regulations like ISO 21434 (2021) help car makers implement risk management and anticipate future threats. The guidelines direct manufacturers to enact safeguards during product development, production, and the entire guaranteed service life of a vehicle. Moreover, car makers are now responsible for the cybersecurity of software-defined cars long after they leave the assembly line and must anticipate security threats that arise during a vehicle’s operation. In addition, WPC Qi 1.3 & Qi2 specifications mandate secure authentication. The most popular wireless charging standard is evolving to accommodate millions of devices capable of being charged wirelessly, with fast charging reaching up to 15 W. Yet, transmitting greater levels of energy wirelessly can lead to technical & safety challenges.
Developers should be aware that a poorly designed or improperly regulated charger could damage or even destroy a connected device. If the wireless charger and smartphone or tablet aren’t compatible, the device’s battery could overheat or even ignite. To prevent these risks, the Wireless Power Consortium (WPC) specification has made public key cryptography with Manufacturer CA certificates and signed Product Unit Certificates mandatory for Qi-certified chargers. Public-private key pairs, signed certificates, and provisioned secure storage subsystems are necessary to indicate a product has passed WPC’s testing and certification process. Secure authentication is thus mandatory for all WPC Qi-certified chargers. However, authenticating a mobile device and Qi charger is relatively straightforward if engineers use the right secure solution.
2nd thing to look for: A solution that requires fewer investments
The tremendous costs of a bad implementation
As Qi is evolving to accommodate millions of devices while also increasing the amount of power it can deliver, the technical, security, and safety challenges inherent to the technology will only grow. Indeed, a poorly designed solution can cause a battery to overheat and explode, leading to far graver consequences than a damaged NFC card. Digging deeper, the key issue is communication. When users put a product onto the wireless charging pad of their car, both must communicate to know when and how much power the charger can safely send.
Additionally, cars have a far longer lifespan than many sink products, like smartphones. Engineers must thus figure out how a vehicle can talk to a product designed five to ten years into the future and still ensure safe and secure communication. Simply put, as the technology trickles down to mainstream and cost-effective vehicles, engineers must find a way to satisfy tighter bills of materials, knowing that a recall due to security or safety vulnerabilities has extremely costly repercussions. At “best”, implementing a “cheap” solution that doesn’t perform well with popular products because it doesn’t meet future needs will negatively impact a brand for many years.
Ready-to-use cryptographic solution with STSAFE-V100-Qi
One of the ways the Wireless Power Consortium (WPC) solved the communication challenge is by mandating public key cryptography with Manufacturer CA certificates and signed Product Unit Certificates for Qi-certified chargers. Thanks to public-private key pairs, signed certificates, and provisioned secure storage subsystems, Qi-compatible products unequivocally demonstrate that they passed the WPC’s testing and certification process, thus guaranteeing they are safe and secure. While using cryptography isn’t new, car makers need a solution that will implement this secure handshake at high speed and efficiency, or the consumer experience will suffer.
The STSAFE-V100-Qi not only demonstrates that it meets all of the criteria set by the WPC, but the ST ecosystem ensures car makers get all the benefits of the standard without additional investments. For instance, ST can provision its device at a secure production facility to guarantee their integrity so that car makers can easily meet the various standards. Our device also comes with tamper-proof and side-channel attack prevention to guarantee the device’s integrity. Additionally, we provide documentation and software tools to help engineers jumpstart their applications. Put simply, integrators should look for a holistic implementation rather than a simple component.
3rd thing to look for: A solution that goes beyond the specification requirements
Choosing the right security certification is a challenge
A lax standard may not be effective, while an extremely stringent one may be too demanding to implement, thus discouraging its adoption by the industry. The WPC specification requires environments to reach a level of security from SESIP Level 2 up to CC EAL 6+ certification. In a nutshell, these certifications ensure that secure hardware protects devices against threats. Device manufacturers should thus consider what security certification to choose when conceiving a secure solution for authenticating Qi chargers and enabling fast charging.
Navigating the waters with a primer on SESIP and CC
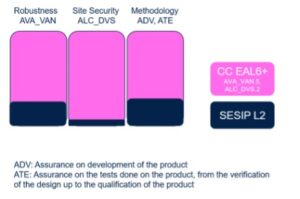
SESIP (Security Evaluation Standard for IoT Platforms) and CC (Common Criteria) are international specifications and guidelines designed to evaluate the potency of information security safeguards. Certification bodies define security policy for all product development and production phases, including manufacturing and personalization. They assess three security pillars (design, methodology, and site security) to determine a product’s vulnerability resistance and protection levels. The evaluations consider, among other things, the functional specifications, the security architecture, and the overall design, including certain feature implementations and threat detection mechanisms. Concretely, guidelines cover vulnerability analysis (AVA_VAN), product development (ADV), testing (ATE), and site security evaluations, which involve functional testing and life cycle support (ALC_DVS).
SESIP is a security certification scheme published by GlobalPlatform and introduced to evaluate IoT components and platforms. The SESIP methodology applies best practices from the Common Criteria (ISO/IEC 15408) framework and adapts them for IoT. In an effort to meet their stringent security requirements, car makers may choose between two common certification schemes, SESIP and CC. The SESIP framework may be more cost-effective to implement than a general scheme like CC, but SESIP is optimized for smaller systems and provides a narrower scope. Indeed, a key difference between SESIP and CC is their vulnerability analysis designed to identify potential security shortcomings due to failures, intrusions, or flaws.
Understanding AVA_VAN levels
SESIP Level 2 is a common certification for IoT that is rated AVA_VAN.2 as it provides a basic level of protection against software attacks and a simple vulnerability assessment. Comparatively, the STSAFE-V100-Qi secure element integrated into a Qi charger meets a CC EAL4+ certification with an AVA_VAN.5 rating, the highest AVA_VAN level. It demonstrates the greatest level of protection against complex software and hardware attacks. More precisely, AVA_VAN.5 covers advanced methodical vulnerability analyses of the security functionalities by evaluating their implementations and testing them against sophisticated attacks. In practical terms, adopting the highest security standards gives car makers the strongest guarantees over the longest period.
The reason we designed the STSAFE-V100-Qi to go above and beyond basic certification requirements is simple. For decades, ST has regularly submitted products to numerous certification bodies for evaluation, and we systematically submit our manufacturing sites and security policies to external audits. Put simply, we take care of this complexity so our customers don’t have to, thus bringing more value to a device like the STSAFE-V100-Qi. By providing an AVA_VAN.5-certified device, we further increase the value of our solution as it can protect against more threats and stay relevant longer.
Rescuing engineers with a complete portfolio
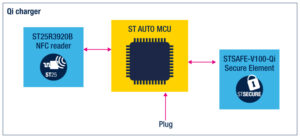
In addition to security services provided by STSAFE-V100-Qi, ST delivers value by offering a cohesive ecosystem of secure automotive solutions that integrate NFC readers. The ST25R3920B NFC reader comes with heartbeat detection, a feature that distinguishes between a power device and a contactless card. Additionally, thanks to its output power, the ST device offers greater sensitivity, and it is NFC Forum certified for CCC digital key applications, which means an OEM could qualify it for more than one application in the same vehicle.
Consequently, designs that integrate both the STSAFE-V100-Qi secure element and the ST25R3920B don’t only protect the things they charge and the people in the car but other products as well, like NFC cards, thus going truly beyond the letter and even the spirit of the current regulations.
