IoT is now nicknamed the “Internet of Threats”, cars get more easily hacked than computers, and improperly encrypting users’ data could bankrupt a company. The world is moving toward more and better encryption methods, because they are necessary to tackle the new challenges users face. ST brings many hardware optimizations to its platform to ensure that encryption and decryption operations do not result in a performance penalty. Whether we are talking about Telemaco, mobile payments, small connected devices, or powerful MCUs, such as the STM32H7, you will find a ST component that has a “crypto core” of some sort. However, this is only one side of the coin. The other side is Cryptolib.
Cryptolib : Cryptographic Modular Middleware
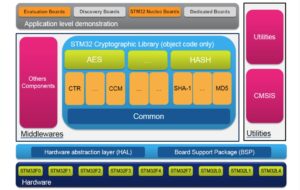
A great crypto core needs something to optimize. Big companies can hire vast teams of experts to implement complex cryptographic methods, or they can simply use X-CUBE-CRYPTOLIB, ST’s firmware library designed to integrate an enormous array of cryptographic methods optimized for its components. It even includes template projects for popular toolchains, such as Keil MDK-ARM, IAR®EWARM (IAR Embedded Workbench®), or GCC-based IDEs. Starting from scratch is now a thing of the past.
In its most basic form, Cryptolib is a middleware that sits under the application, and above the hardware. This structure allows it to be compatible with all of the STM32 MCUs. As a result, when one prototype requires another microcontroller, whether to obtain more computational power, or lower the energy footprint, Cryptolib contains all the necessary firmware to switch hardware platforms without having to rewrite the application. The middleware simply takes the software code and adapts its execution during compilation. Furthermore, because Cryptolib is a modular library, it is possible to easily add algorithms, or customize them to change memory management, or execution speed, making the package future-proof.
A Method for Every Need
The number of algorithms offered by Cryptolib is huge, and will cover the needs of very nearly all projects. For instance, AES–256 is a symmetric-key algorithm, which means there’s only one key to cipher and decipher. Used by governments, it is extremely reliable and fast. It can encrypt a text in a way that is self-decipherable, as long as the user has the right password.
SHA–512 (Secure Hash Algorithm) generates a 512-bit hash that can protect passwords, or digital signatures, because it is a one-way function, which means there is no way to decrypt it back. In other words, a hash cannot pass through a function to convert it into plain text. As a result, the user will have to enter what the plain text is supposed to be, the algorithm will encrypt it, and then compare the obtained hash with the one in the system. If they match, it means the plain text is correct. Therefore, the only way to theoretically crack a hash is to use a brute-force attack, meaning trying every single combination possible.

Cryptolib also facilitates the use of the Elliptic Curve Digital Signature Algorithm (ECDSA). An elliptic curve cryptographic (ECC) approach is one of the most powerful methods for encrypting data, because it uses a mathematical problem that can’t yet be solved with an algorithm. Hence, it is increasingly popular on the web, data centers, and government agencies, to prevent eavesdroppers from deciphering an intercepted message. It offers an even higher level of security than other public-key cryptographic systems, like RSA, but at a fraction of the size. For instance, the equivalent 256-bit ECC public key would have to be 3072 bits if one was using RSA.
Certified!
Last July, Cryptolib’s implementation of the three methods mentioned above was certified by the Cryptographic Algorithm Validation Program (CAVP). Used in America and Canada, it validates the implementation of cryptographic algorithms according to the standards established by the Federal Information Processing Standard (FIPS), and National Institute of Standards and Technology (NIST). Hence, because Cryptolib is now accredited, any product that relies on this middleware can be directly submitted to the FIPS for security testing, because ST already took care of the validation process. Whether one is making a point of sale terminal, a smartphone with a fingerprint reader, or the simplest access point, Cryptolib offers a simple way to implement algorithms that have gone through the most stringent certifications, so you can use them with total peace of mind, and know that going from prototype to mass production will be a lot simpler.
It is possible to obtain Cryptolib by asking for it on ST’s website. It is available for free under ST’s Software License Agreement, and a request usually takes 48 hours to validate.
